Explain Different Types of Phishing Techniques
Minimal or no dollar amounts assigned to land non-depreciable land improvements building or other longer-lived assets. List the types of threats that can be.
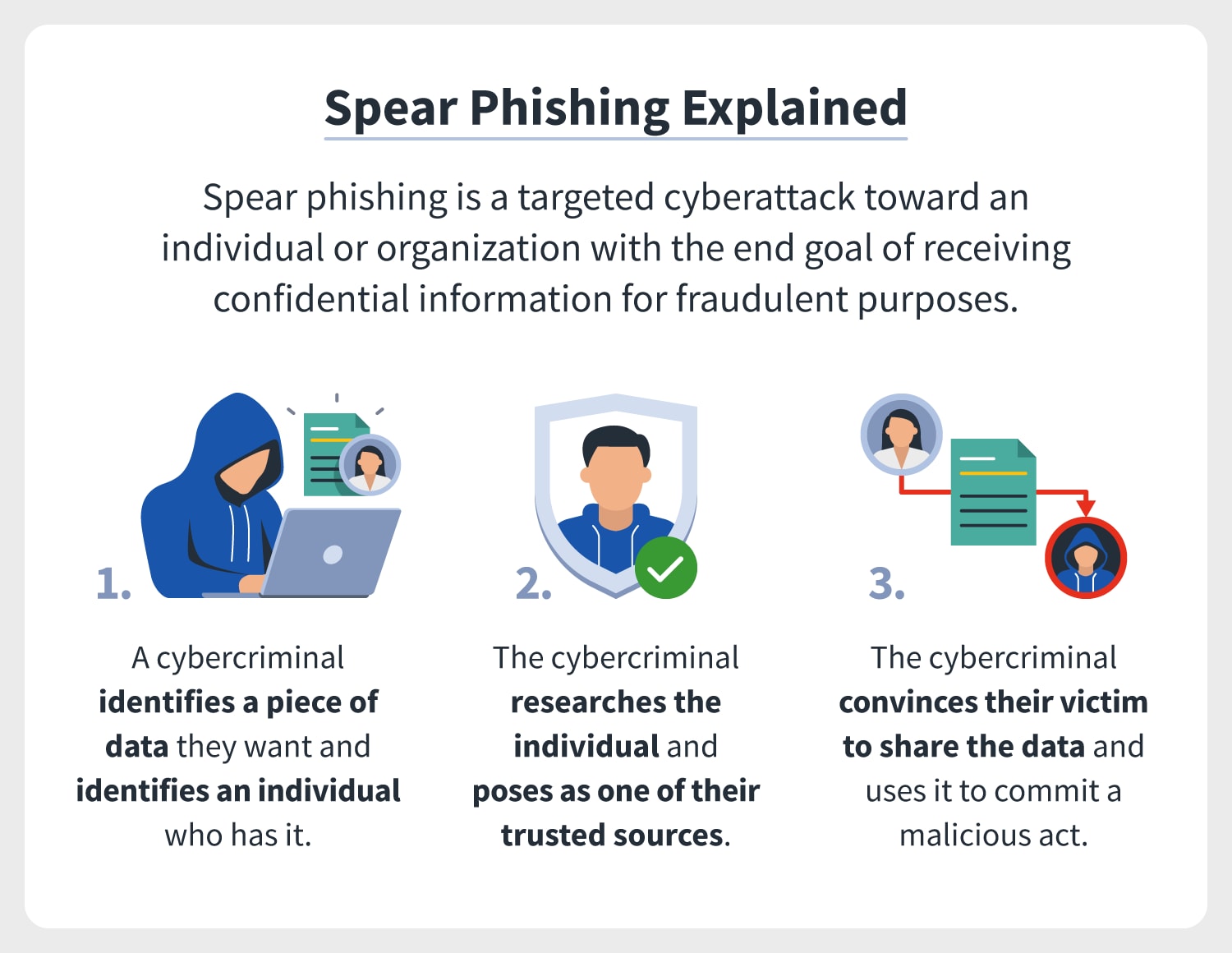
Spear Phishing A Definition Plus Differences Between Phishing And Spear Phishing Norton
It is designed to expose a WCF service as an ASMX.

. Describe and five steps to implementing a Zero Trust model in your organization. Describe the components of Zero Trust security. It supports different types of protocol to communicate with client and different types of encoding to transfer the data over the internet.
Explain Zero Trust networking. A healthy dose of online skepticism and attention to detail will get you a long way though. So basically binding is nothing but it is a way of communication between client and service as per client need.
DOWNLOAD FREE AVAST ONE Get it for Android iOS Mac. Ie assets with different recovery periods. If an official-looking email sent you a link make sure the URL its taking you to looks correct.
Describe techniques hackers use to gain control over resources. Mixed asset types in the same unit or group. Learn about different types of property crimes like burglary theft.
Anyone actually representing a website or service you use wont actually need your password so dont. This binding is provided by the BasicHttpBinding class. In this article we define malware introduce its many different types and explain how it works.
Building structural components or leasehold improvements classified with improper shorter-lived 1245 recovery periods. Describe the Zero Trust approach to security in Microsoft 365. We also describe the warning signs of an infected device and explain how to prevent it with Avast One our world-class anti-malware protection.
Property crime is defined as crimes aimed at properties rather than people. INSTALL FREE AVAST ONE Get it for PC Mac iOS. Phishing can take many different forms so theres no single way to defend yourself.
Describe techniques hackers use to compromise data.

What Is Phishing Avoiding Email Scams Attacks Fortinet

6 Common Types Of Phishing Attacks

Phishing What Is Phishing Phishing Types And Techniques Techniques Meant To Be Type
No comments for "Explain Different Types of Phishing Techniques"
Post a Comment